The Concept of a "Nmap Zombie": A Comprehensive Exploration
Related Articles: The Concept of a "Nmap Zombie": A Comprehensive Exploration
Introduction
With great pleasure, we will explore the intriguing topic related to The Concept of a "Nmap Zombie": A Comprehensive Exploration. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: The Concept of a "Nmap Zombie": A Comprehensive Exploration
- 2 Introduction
- 3 The Concept of a "Nmap Zombie": A Comprehensive Exploration
- 3.1 Botnets: The Foundation of "Nmap Zombies"
- 3.2 The Role of Nmap in Botnet Operations
- 3.3 The Importance of Understanding "Nmap Zombies"
- 3.4 FAQs about "Nmap Zombies"
- 3.5 Tips for Using Nmap Responsibly
- 3.6 Conclusion
- 4 Closure
The Concept of a "Nmap Zombie": A Comprehensive Exploration

The term "Nmap zombie" is a misnomer, often used to describe a scenario where an attacker leverages the power of numerous compromised computers, known as "zombies," to perform malicious actions. While Nmap, a powerful network scanning tool, can be used in such scenarios, it is not inherently responsible for creating or controlling these "zombies."
To understand the concept of a "Nmap zombie," it’s crucial to delve into the broader context of botnets, the technology behind them, and the role that tools like Nmap can play in both creating and mitigating such threats.
Botnets: The Foundation of "Nmap Zombies"
A botnet is a network of compromised computers, often referred to as "bots" or "zombies," controlled by a single attacker, known as the "botmaster." These compromised machines are typically infected with malicious software, often through phishing emails, drive-by downloads, or vulnerabilities in software applications. Once infected, these computers are remotely controlled by the botmaster, who can use them to execute various malicious activities.
The Role of Nmap in Botnet Operations
Nmap, a versatile network scanning tool, is frequently used in the context of botnets, but its role is multifaceted and can be both beneficial and detrimental depending on the user’s intentions.
1. Botnet Creation and Management:
- Scanning for Vulnerable Targets: Nmap’s powerful scanning capabilities allow attackers to identify potential targets for botnet infections. By scanning networks and systems for open ports, known vulnerabilities, and running services, attackers can pinpoint machines that are susceptible to exploitation.
- Exploiting Vulnerabilities: While Nmap itself does not exploit vulnerabilities, the information gathered from Nmap scans can be used by attackers to deploy malware that exploits known vulnerabilities, turning vulnerable machines into bots.
- Botnet Communication: Nmap can also be used to establish communication channels between the botmaster and the compromised machines. By configuring specific ports and services, attackers can set up command-and-control (C&C) servers that allow them to communicate with and control the botnet.
2. Botnet Detection and Mitigation:
- Identifying Infected Machines: Security professionals can utilize Nmap to scan networks and systems for signs of botnet activity. By looking for unusual port configurations, services, and network traffic patterns, they can identify machines that may be compromised.
- Analyzing Botnet Behavior: Nmap can help security professionals understand the behavior of botnets by mapping network connections, identifying communication patterns, and analyzing data flows. This information can be crucial for identifying the botnet’s command-and-control infrastructure and mitigating its impact.
- Disrupting Botnet Operations: Nmap can be used to disrupt botnet communication by blocking access to C&C servers or by interfering with botnet traffic. This can help to limit the botnet’s ability to operate effectively.
The Importance of Understanding "Nmap Zombies"
Understanding the concept of "Nmap zombies" is essential for both security professionals and users alike. By recognizing the potential dangers of botnets and the role that tools like Nmap can play in their creation and mitigation, individuals and organizations can take steps to protect themselves from these threats.
For Security Professionals:
- Developing Robust Security Practices: Understanding the techniques used by attackers to create and manage botnets enables security professionals to implement better security practices, such as patching vulnerabilities, using strong passwords, and deploying intrusion detection systems.
- Identifying and Mitigating Botnet Threats: By leveraging Nmap and other security tools, security professionals can proactively identify and mitigate botnet threats before they cause significant damage.
- Analyzing Botnet Activity: Understanding how botnets operate allows security professionals to analyze botnet activity, identify the botmaster’s intentions, and develop strategies to counter their attacks.
For Users:
- Raising Awareness: Understanding the concept of "Nmap zombies" helps users recognize the importance of maintaining strong security practices, such as using secure passwords, keeping software up-to-date, and being cautious about suspicious emails and websites.
- Protecting Personal Information: Awareness of botnet threats encourages users to be more vigilant about protecting their personal information, such as credit card details, social security numbers, and login credentials.
- Reporting Suspicious Activity: Users can play a crucial role in combating botnets by reporting suspicious activity to their internet service provider or security professionals.
FAQs about "Nmap Zombies"
1. Can Nmap be used to create a botnet?
While Nmap can be used to gather information that attackers can leverage to create botnets, it is not a tool for directly creating or controlling botnets.
2. Is Nmap inherently malicious?
Nmap is a powerful and versatile network scanning tool that can be used for both legitimate and malicious purposes. Its use is dependent on the user’s intentions and the context in which it is employed.
3. How can I protect myself from becoming a "Nmap zombie"?
- Keep your software up-to-date: Regularly update your operating system and software applications to patch known vulnerabilities.
- Use strong passwords: Avoid using easy-to-guess passwords and enable two-factor authentication whenever possible.
- Be cautious about suspicious emails and websites: Don’t open attachments or click on links from unknown senders, and avoid visiting suspicious websites.
- Install and maintain antivirus software: Use reputable antivirus software and keep it updated to protect your computer from malware.
4. What should I do if I suspect my computer has been compromised?
- Disconnect from the internet: To prevent further damage, disconnect your computer from the internet.
- Run a full system scan with your antivirus software: This will help to identify and remove any malware that may be present.
- Contact your internet service provider: Inform them of the situation and seek their assistance in resolving the issue.
5. How can I identify a "Nmap zombie" on my network?
- Monitor network traffic: Look for unusual network activity, such as high bandwidth usage or communication with unknown IP addresses.
- Check for unusual processes: Examine your running processes for suspicious applications or programs that you don’t recognize.
- Scan your network with Nmap: Use Nmap to scan your network for open ports, services, and vulnerabilities that may indicate a compromised machine.
Tips for Using Nmap Responsibly
- Understand the legal implications: Be aware of the laws and regulations governing network scanning in your region.
- Respect network security: Only scan networks and systems that you have permission to scan.
- Avoid scanning sensitive networks: Do not scan networks or systems that you are not authorized to access.
- Use Nmap ethically: Do not use Nmap to engage in malicious activities, such as hacking or denial-of-service attacks.
Conclusion
The concept of a "Nmap zombie" highlights the complex relationship between powerful tools like Nmap and the potential for malicious activity. While Nmap itself is not responsible for creating or controlling botnets, it can be used by attackers to gather information, exploit vulnerabilities, and manage botnet operations. Understanding the role of Nmap in the context of botnets empowers security professionals and users to take proactive steps to protect themselves from these threats. By employing robust security practices, staying informed about the latest threats, and using tools like Nmap responsibly, individuals and organizations can mitigate the risks associated with botnets and ensure the security of their systems and networks.






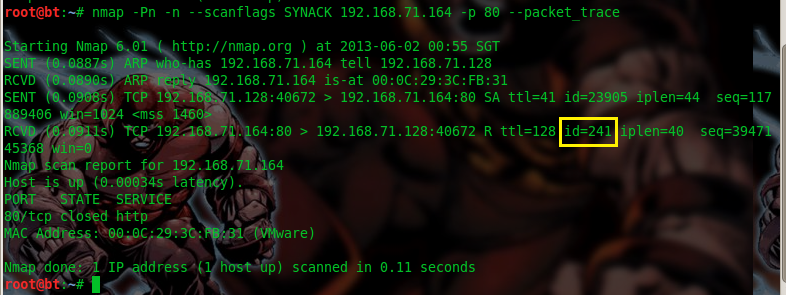
![Zombie scanning with Nmap - Kali Linux Network Scanning Cookbook - Second Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781787287907/files/assets/image096.png)
Closure
Thus, we hope this article has provided valuable insights into The Concept of a "Nmap Zombie": A Comprehensive Exploration. We hope you find this article informative and beneficial. See you in our next article!